While studying for networking exams it’s always important to analyze the packets, afterall the devil is in the packet, but for most just starting out (and to be honest myself included still) reading packets is not necessarily straightforward. With the sheer amount of connected devices unless you have your filters setup you will get data overload which is going to hurt your abilities to find that packet flow you were looking for. I’ve been a big fan of the metageek product called Eye P.A. which is a Windows based packet analysis tool focused on Wireless technologies, but sometimes (ok, not sometimes, most of the time) you want to view the PCAP files from a Mac or share them with others, that’s where the products we are going to talk about today come into play. For those of you playing at home, get your blanket ready, yes we are talking about cloud based packet tools. I’ve looked at a couple of the tools out there and have to say I’m impressed with what we have so far, this could be a potential market that has not been tapped into much yet.
CloudShark
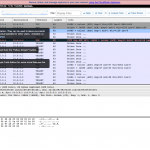
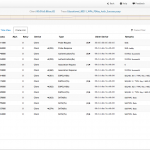
CloudShark has been around for a bit now but I never really started using it until I wanted to find a tool that a person in the field could collect the data using Airpcap cards or similar and then upload somewhere for post analysis by a senior engineer. CloudShark is basically a direct implementation of Wireshark but web-based instead of being installed on your local machine. The nice thing about this is that if you are familiar with Wireshark then it is an easy transition from one to the other. But the web-based viewing of the PCAP file isn’t the only plus that you get, if you purchase the appliance (which is spendy) you have the ability to upload, store, share, and collaborate with the capture files. Being a remote member of a team this would be huge for troubleshooting issues, I could review a capture file, add some annotations about where I see potential issues, and then others could see those annotations instead of me telling them to go to packet 50 of 1000. Recently Cisco Meraki announced the ability to send capture files directly from their devices to the CloudShark setup. This is a great feature for MSP and remote NOC groups. Analyzing the data requires the data to be captured, and I personally think that is the hardest aspect. Let me rephrase that, getting quality data you can trust captured is the hardest aspect! So by having the ability to directly upload you bypass that issue. While CloudShark gives you that direct Wireshark replacement, the one thing it doesn’t do a great job of is putting things into simple flows. I would love to see CloudShark have a plugin based extension model where we could create an 802.11 Wireless plugin that would show us EAP exchanges, WPA/WPA2 Pre-shared key exchanges, client roam events, etc. For pricing information you’ll need to contact them as they are working through pricing models still as this is a new product.
Wizshark by AirTight
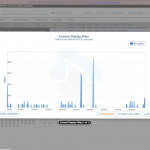
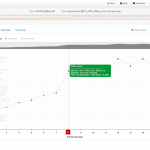
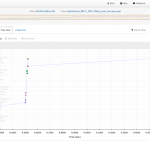
While we were at WFD5 visiting AirTight (creators of WiFun!) we got a sneak peak at a tool they wrote to assist them in troubleshooting packets. Now first of all that is my kind of team, I’m all about creating web applications to make life easier. I’ve wrote my own project, resource, and inventory management engine (aka prime – not the Cisco Prime) for use at the past few VARs I’ve been at allowing us to easily manage projects, inventory, expenses, etc. I’ve also wrote document management systems before, and come up with countless numbers of scripts to automate tasks. So when I saw that they made their own tool I thought awesome, but then at the same time thought why not just integrate with CloudShark like others? Well the reason I can find is that really AirTight was looking at the packets differently, not so much about all the little details about every packet but more about the flow, and how it effects Wireless authentications for example. Wizshark is going the direction of Eye P.A. in that they want to provide a meaningful simple view of the packets that anyone can understand, whether you are a junior or senior engineer. The example files that Wizshark shared with us when they provided our beta details shows various authentication packet flows allowing you to see where the issue(s) occur. When you hover over a packet event in the timeline view you get a tooltip hover with some of the packet details which by clicking on will show you the full packet. I like this, but find it tricky to use to be honest. The screen automatically fills up with 1000 packets, so the single packet gets hard to click on. After the post was published AirTight informed me that there is a zoom. Once you have a selection of packets selected right above the timeline style view there is another section that you can move the sliders around to zoom in. I’m also not a fan of the packet detail view window, I would love to see them utilize more of the HTML5 data views and possible some of the jQueryUI/jQuery Mobile design elements for a better user experience. Problem with Wizshark is that you need to send the data there after doing a capture, there is no realtime transfer of the capture file, hopefully soon we can expect that? I like the direction Wizshark is going if we can combine features from Omnipeak’s Expert rules and Eye P.A. feedback rules to create a web based version. I could see this being very helpful to people learning the trade. I also wish I could annotate the files, seeing as I can share with others it would be great to annotate an issue like CloudShark can for others to view.
Finale Thoughts
Both tools serve a purpose, if you are an organization that is deep into packet analysis then you really should be looking at something like CloudShark. If you are just looking for doing basic analysis and focused primarily on Wireless then Wizshark is going to be better. It will be interesting to see how these two products adapt, neither work that well on a mobile platform and I think that could be the deciding factor going forward. I need a tool that I could use from any device any where.
* For the purpose of this blog post I used the generic samples as to not release any personal/customer data.


“the devil is in the packet”? Really? 😛 Awesome. I guess “packets never lie” is out the window now, eh?….possessed packets! Good blog Blake. Our engineering team is continually improving WizShark, and we’d love for some protocol analysis experts to give it a try and to offer feedback! Thanks for checking it out Blake!