Last year was the year of BYOD when it came to buzzwords. Everyone was hopping on the bandwagon and using that term like crazy. The funny thing is that it really wasn’t anything new! Having worked in the higher ed space at the beginning of my career I’ve always had to deal with people bringing their own devices and expecting them to get connected. Students were bringing their computers from home and putting them on the dorm network requiring their TCP/IP stacks to be rebuilt because they use AOL at home, or trying to get onto the campus wide wireless network that had a captive portal requiring browsers to always be launched. BYOD just wasn’t anything new to me nor could I really get on board with it as a new craze. Now comes 2013 and we need a buzzword to get us through all the marketing pitches, well that buzzword is AVC, or Application Visibility Control.
What is AVC?
Now one could argue that this isn’t anything new either as we have had Netflow for awhile now but we really haven’t had the data presented in this way before right from the vendors. AVC is simply visualizing traffic destinations in such a way that you can see how much of the data on your network is destined for HTTP/S for example and what sites such as Facebook, Twitter, etc. AVC also allows you to see how much data is for streaming services such as iTunes, AirPlay, etc.
Why Should I Care?
So why should I really care about this? What does this give me? As we become more of a connected society our bandwidth consumption has increased tremendously. Companies constantly struggle with having enough bandwidth do get their business tasks accomplished while meeting the needs of their employees. AVC allows a company to really see where their bandwidth is going and allows you to control it’s usage, hence the name. We can create profiles to drop traffic so instead of relying on a proxy server to do that for us we can stop it at the point of presence for a connection. Or maybe you don’t really need to drop it, you just want to be able to say what your top bandwidth usage is. A great example is when I installed my Meraki switch at my house, right away I was able to see that my Samsung Tab 8.9 that ran a simple security camera app was creating close to 158GB worth of traffic every 24 hours on my network, I wouldn’t have known that without AVC! I’ve also found how much our Netflix adds to our bandwidth cap usage each month.
The Future
Network design is really starting to change, we are progressing away from a switch port VLAN mapping to more of a traffic/user/device mapping with technologies like Software Defined Networking, policy based routing, and identity & device profiling. This new era of a dynamic network is an interesting one and will be interesting to see how all the new technologies come together to reshape how we architect networks. Ultimately in order for this new design concept to work we need the right tools, networking vendors are being forced to become software companies as well. The big names such as Aerohive, Aruba, Cisco, Meraki, for example all have this in their GUIs now at least for wireless traffic. I think Meraki does it best though in how they present the data to you. Their UI’s have always outshined the competitors, hopefully Cisco will take note of that as the Meraki talent is brought into Cisco post-acquisition. Data sources will also be key for the success, deep packet inspection is really the best solution instead of relying simply on DNS resolutions or known ports. When I look through my logs every now and then I’ll see WoW traffic, something that I don’t ever play, but according to Meraki’s AVC I’ve passed 2GB worth of traffic over a week, this could simply be web ad data, which flaws the data slightly.
Does AVC seem all that important to you? Chime in on the comments! I will leave you with a snippet from my Meraki dashboard for a week in December, this was a light week as I wasn’t home the entire time.
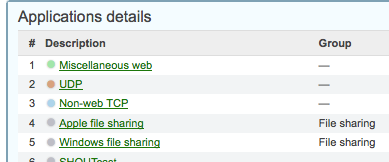


Looks like my first time around I was foiled by the spam filter – d’oh!
I completely agree the IT “pros” have been navigating BYOD for quite some time. In my opinion, the biggest technology driver that has caused the recent phenomenon is smartphones and tablets, but I guess from an acronym perspective “BYOPoT – Bring your own phone or tablet” wasn’t nearly as catchy and could be misinterpreted 😉
I also agree that AVC will, from an admin’s perspective, have a much greater impact. Rather than gathering the data via traditional netflows, the value in instant presentation of the data not only speeds up troubleshooting, but also offers the ability to present the client the option to control application usage with their staff without purchasing more bandwidth. This is especially important in locations where bandwidth is either at a premium or there is limited selection of providers (such as where I am).
Meraki from day 1 definitely excelled in the presentation of this data, here’s to hoping they continue to build on this momentum post-acquisition. I am also interested to see how the other vendors address this or build on it. Obviously when you look at organizations like Cisco, like Aruba they have both wired and wireless offerings and some level of this capability already, what would be ideal is to “standardize” this capability so that multi-vendor environments can get a single pane of glass view as opposed to having to jump across to different dashboards.
Blake, an application aware solution alongside policy options is critical. Having the ability to not just filter but intelligently filter/study at the source is crucial in serving business and non-critical traffic. Realizing what is waste and needed provides decision makers and LOB POCs with options based on granular data. I’m playing around with packetshaper from bluecoat and various Aruba solutions. Lync is in pilot stage and folks are eager to adopt guest network solutions. QoS can be useful as are hard bandwidth caps but like you have written, we are seeing an influx in application as well as a myriad of endpoint devices…not just (jokingly stated)”xp” anymore! To top it off “dynamic” 802.11 medium access is key as network transport.
Good post